How to secure Confluence? The actionable guide

How to secure Confluence
What you will get from this guide
Information is power. However, it can be disastrous when this power gets into the wrong hands. In the previous year alone, IBM's Cost of a Data Breach report recorded a 2.6% increase. This increase brings the cost to $4.35 million in 2022.
The value of information that flows around on pages is enormous and it is necessary to safeguard these information. It is a fact that Confluence does not encrypt your data out of the box. Therefore, the onus is on you to control and safeguard the flow of information in your organization.
All these factors make administering a large collaboration workspace like Confluence a herculean task. However, if you don't have the resources to hire a whole team to safeguard your IT space, following a few best practices guides is a must.
Although only some practices in this guide will apply to your situation, the principles are easily transferable. Also, none of these practices provides 100% security; they merely reduce the impact and risk of your system being compromised.
This article teaches the 11 easy-to-follow guides you can use to secure your Confluence site. Many factors, like installation environment, database servers, network, firewall, users, administrators, etc., were considered. Follow closely.
Secure your installation directories
This section is for businesses who want to install and run Confluence from their infrastructures. You can jump to the next guide if your organization uses the Confluence cloud.
Although Confluence is built purely on Java with no native components and this makes it resistant to buffer overflow vulnerabilities. However, the security responsibilities of your installation directory, home directory, and storage are on you
One of the first steps to ensure security is to run Confluence with a non-root user account. When you start Confluence, it runs the user it was invoked under. Giving root access to such a user can lead to complications for both the local machine and the Confluence instance.
If you are installing Confluence on a Linux-based OS, type the following command in the console:
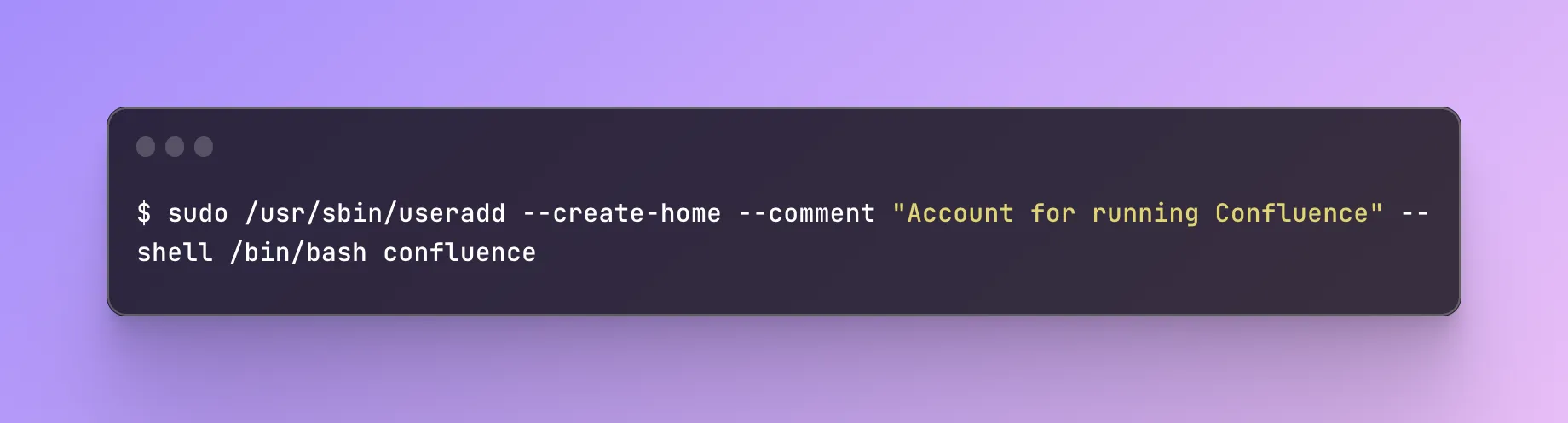
However, if you use windows, you can enter the following in the windows command prompt:
.webp)
Also, limit the users who have access to all Confluence directories. The principle of least privilege maintains that a user should have access to just enough information to complete his required task.
Manage permissions at the site, space, and page level
Continuing with the principle of least privilege, use a top-to-bottom approach, similar to the Identity and access management (IAM) used by cloud providers. At the site level, give permissions that all your organization members share.
Once you get to the level of spaces, give out space-level permissions. Information specific to the HR department should not be visible to your software engineers, nor should theirs be visible to the business analysis team. The permission for any data that the whole workforce needs should be given at the site level.
At the microscopic level, Confluence also allows you to set permissions at the page level. If the information you want to restrict access to is not organized into spaces, you can limit access to them and invite only the individuals necessary.
Furthermore, Confluence also permits you to restrict the permission of a page or space to view. A typical example is company policy. While you would want all your employees to have access to such information, especially when onboarding new members, only the Human Resources Department and other executives should have access to edit it.

Maintain an active subscription to security alerts
Register your contact details when setting up Confluence. This will ensure that you promptly receive all advisory and security alerts.
Receiving timely notification of a compromise enables you to swiftly swing into action and follow your organization's damage control protocols. This ensures that the damage to your system will be as minimized as possible.
Also, during your periodic audits, ensure that you revise and keep your contact details up to date.
Run your database in a secure environment
Confluence does not inherently encrypt your documents. The onus is on you to ensure that you are running the database attached to your Confluence in a safe environment.
One of the ways to do this is to install a firewall in the compute instance running the database. Only the host running your Confluence should have access to the instance. You can use iptables and other database security tools to ensure this.
Your database documentation will have a detailed description of how to effect this. If you are using a Cloud Service like the AWS RDS, configuring and limiting access to only the Confluence host can be completed from the console.
Limit the number of administrators
Merely reducing your number of admins could make your system more secure. The tighter the cycle of users with admin privileges, the more secure your workspace is. The number of your Confluence administrators should be limited to just such a number as enough to execute the admin functions.
Your administrators should maintain two separate accounts - the account for administration tasks should be separate from the one used for day-to-day work. An extra level of awareness will be involved when they sign into the admin account. They know they are about to take on more responsibilities, which will minimize accidental loss of credentials.
Avoid rookie mistakes like using easily guessed usernames like ‘admin’, ‘root’, or ‘super user’ for your admins.
Reduce the number of people you invite into the confluence-administrators group. This is a default "supergroup" that all have access to all contents on your system, including restricted pages. Other than this, they also have admin functions and privileges.
The timeouts for admin sessions should be as short as possible, although not too short to disrupt the flow of their daily work. They should be prompted for their password periodically while they use their system.
Use IP tables, firewalls, and gateways to lock down the administration web pages to specific IP addresses. Depending on your installation, OS, and infrastructure, you can use Apache reverse proxy template to implement this. Also, your admins should notify you whenever they want to embark on any travel. This will enable you to review their IP addresses when needed; but this should be an exception and not the rule.
Limit incoming and outgoing connections
Your database, for example, should only be accessible by your Confluence host account. Also, enforce HTTPS or SSH protocol for all incoming connections.
Other ways to limit incoming connections include firewalls and proxy servers at different endpoints in your network. Doing this helps you avoid Server-Side Request Forgery(SSRC) attacks.
Allowlist is another way of restricting incoming and outgoing connections. Macros, external site contents, and other juicy features of Confluence rely on this.
Administrators can specify which content is allowed for incoming and outgoing connections. This method can be used in the following ways:
- HTML macros
- Gadgets
- Widget Connector Macro
- RSS Feed Macro
by adding URLs to the Allowlist.
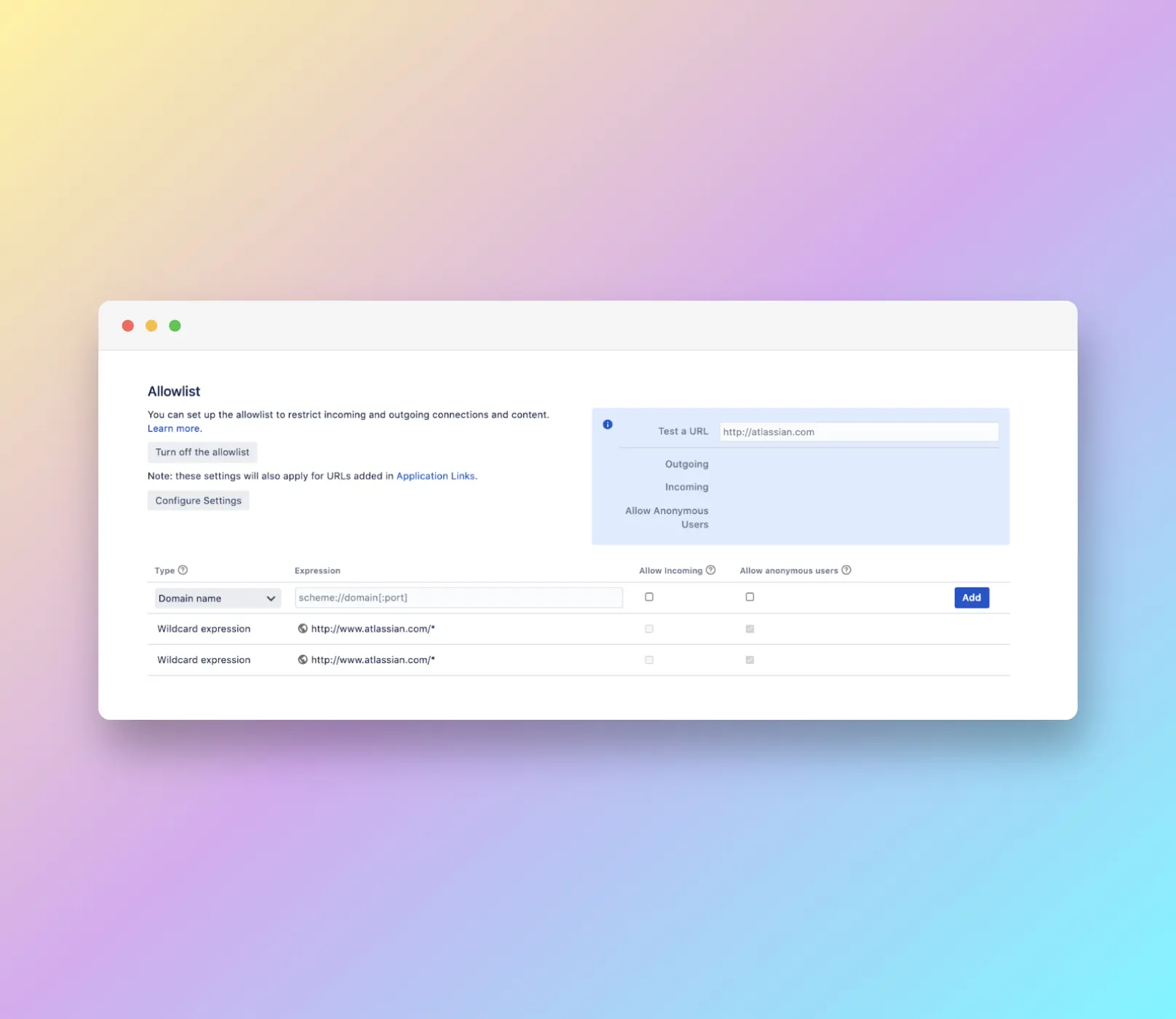
Follow these steps to add a URL to the Allowlist:
- Go to settings, General Configuration, and then Allowlist.
- Enter the URL or expression you want to expose.
- Choose its type
- Choose Allow Incoming option if you want to allow authenticated users.
- Choose Allow anonymous users if you want unrestricted access.
- Select the add button
Limit the rate of API requests
An effective way to reduce the risk of using brute force to hack the passwords of your admins or employees is to use a third-party program like Fail2Ban. This program integrates into Confluence to restrict the limit of login attempts per user.
Another classic method malicious actors use is denial of service attacks. You can use rate limiting to block incessant REST API requests from anonymous users. You can either configure your system to turn them back after a certain logic is not met or just simply limit the number of requests that end users can send per minute.
Data loss prevention
Because of the inherent nature of Confluence, your organization is at risk of exposing various types of sensitive data. This includes:
- API keys and access tokens for third party services
- SSL certificates
- Cryptographic keys
- Database credentials
- Password and login credentials
- Personally identifiable information (PII) of customers
For example, if an employee accidentally pastes an AWS access key into a Confluence page that is shared with other team members. Anyone with access can make changes and incur charges on the company’s resources.
Mistakenly uploading the spreadsheet containing customer name, phone number, address, and email address into a Confluence page could expose this for fraudulent activities or other malicious intent.
Data loss prevention is an access control which ensures confidential information is kept on a need-to-know basis. It involves:
- Scanning content within messages and files to determine if an unauthorized disclosure of information has occurred.
- Provides alerts and analytics that help companies understand risk and employee behavior over time.
Scan with elba your entire existing Confluence instance, configure multiple different DLP policies, apply policies to particular locations, create multiple detection rules, and provides a comprehensive approach reducing false positives and noise.
Log your access information.
To continue the data loss protection theme, ensure you have a data policy on logging, monitoring, and analyzing important administrator and employee actions. This could range from creating pages, sharing pages, and increasing security privileges to any other activity that may be pertinent to your business need.
Logs help you to find out who is executing every activity on the system. This way, you can quickly identify and respond to unusual activities. You can find the records in the installation directory. Review such log data and settings during your annual audit.

Perform regular security checkups
A biannual security audit will help you identify new threats and improve your security policies/procedures. Malicious actors do not ever stop learning new tricks to penetrate your system. Therefore, you cannot rely only on obsolete practices without improving them.
Perform exercises with hypothetical “what if” situations. Examples are: “What is the worst thing that could happen if an aggrieved privileged user turns against the company?”; “What can we do if one of our admins loses his password during a vacation?”. This helps to improve response, minimize damage after security breaches, and adequately cater for unforeseen circumstances.
Accurately document your security policies, measures, and practices in a safe and easy-to-access place. This single source of truth method ensures that after upgrades and migrations, every system maintainer has a checklist of measures and rules to apply.
A security checkup should precede each major upgrade. Compare your current set-up with the recommendations before and after the upgrade.
Manage User Accounts
Finally, the users are the most critical aspect of securing your Confluence. It is a well-known security rule that humans are the most vulnerable link in securing a system. This is why good user management practices will help prevent user account details from falling into the wrong hands.
Where possible, you should consider integrating Confluence into an identity provider for two-factor authentication and single sign-on.Two-factor authentication is a powerful tool to prevent compromising accounts, even if the details fall into the wrong hands. Also, SSO removes the burden of creating unique passwords from the end-users while relying on the robustness of the SSO provider.
Consider using access tokens for integrations, instead of the basic authentication (username and password). First, it is more secure and removes the burden of entering passwords that could compromise them.
Basic authentication is less secure. If you want to be more radical, disable basic authentication. Configuring single sign-on with an identity provider can help you move away from this old practice.
Follow these steps to disable basic authentication:
- Go to the administration option of your Confluence site.
- Next to the default auth method, select Actions and click Edit.
- Next, untick the show default login form checkbox.
- Select Save configuration
To disable the API calls:
- Go to the Auth method page as mentioned above.
- Toggle the Allow basic auth on API calls option.
Have a standard operating policy for off-boarding employees when they leave your organization. Disable the accounts, replace them with anonymous IDs or outrightly delete them. Keep the flow of information as tight as possible.
TL;DR
Administering a large workspace like a Confluence site can be overwhelming. This is because of the number of factors you need to account for. You are especially disadvantaged if you are a small business with no extra resources to allocate to an IT department. However, implementing the best practices highlighted in this guide will help you secure your Confluence site.


